Email of the day on cyber security and the Internet of Everything
I worked on disc firmware in the early 70s and then continued with computer security consulting to the usual agencies with the usual clearances.
Your correspondent (Ed. on May 4th) seems to have been stimulated to make comment as a result of an FT article. Having been interviewed about security by the FT in the mid-80s, I soon learnt that any statement made to a journalist was likely to be mangled to the point of incoherence.
I wouldn't expect to find insight on finance in a security journal so reacting to a story about security in the finance section of a newspaper without checking the story and the details sets the scene for confusion and misrepresentation.
The "former R&D executive" misses the point of the exploit completely and sets up a strawman about the chain of integrity. The whole point of the attack vector in this case is that no spyware "has to be designed in" .
No-one has made any claim of secret implementations of spyware across "multiple US companies". The "spyware" is not "designed in" as the attack vector uses firmware update capability to introduce the trojan.
This is not new and even in the 70s and 80s we were advising our clients on threats from any updateable firmware whether in drives or in peripherals such as laser printers.
What is new is that someone has published details and it is not surprising that an individual or company needs to be outside the UK and the US to risk publication even of well-understood techniques in this area.
Kaspersky's researchers seem to find aspects of this "sophisticated" but that is probably because their origins are in anti-virus scanning rather than general computer security or high integrity systems.
Even interested hobbyists and hackers have shown how to reverse engineer and modify the firmware of standard off-the-shelf hard drives without any expensive equipment, documentation of the chips or source code of any kind.
Regarding a "very senior executive in the computer security business"; well, I have been one of those and found many others with that description to be completely clueless technically.
As for the advice to use some named anti-virus products, if you check in the deeper parts of the security world, you will find those are referred to as "Silent Partners of the NSA". As a junior engineer who ordered the very first encryption chips to be imported into the UK in the late 70s, I quickly learnt that others had a great interest in my activities and was soon required to inform our friends in Cheltenham of my progress on a regular basis.
I have added two relevant attachments and if you take a few seconds to glance at the sentences that I've highlighted in yellow, you will get some insight beyond the misrepresentations of the FT and Reuters.
There are a few "journalists" who can comment more sensibly in the area and some publish at technology site Ars Technica.
This is a short overview of how a hobbyist can put a backdoor on a hard drive.
Dan Goodin has a degree in English and a Masters in journalism but covers aspects of security in a readable manner.
His overview of the Kaspersky/NSA story is here.
Hope this clarifies the picture.
Thank you for taking the time to share your experience of what is an important sector. I am constantly impressed by the breadth of knowledge exhibited by our subscribers and your combined generosity in sharing it. This is perhaps the Service’s greatest strength and thank you all for contributing to our Empowerment Through Knowledge theme.
The original Kaspersky report and the additional annotated report, focusing on how to gain access to a hard drive via a “back door”, are well worth reading as you say. Thanks also for the additional links to the above news items.
The explanation of how Kaspersky was able to develop sink holes for returned information by securing expired web addressed that had been used by the Equation Group is fascinating. While we might conclude this was an error on behalf of the group, another interpretation is that the addresses were simply no longer required and that the group has moved onto something else. When it comes to the defence sector it is reasonable to conclude that whatever is now public is already outdated compared to what is in development or non-public.
Regardless of how one feels about Edward Snowdon’s actions there is no doubt that the information coming from his disclosures is having an effect. It has forced some to work harder to conceal operations and has been a benefit to those wishing to use the existence of well-funded hacking groups to further their own geopolitical aims. Polite informative comments are always welcome.
I don’t claim any specialised knowledge of internet security. In some regards I feel like Socrates in that “All I know is that I know nothing”. However my feeling is that the revelation that it is possible to infect firmware will necessitate a comprehensive overhaul of corporate security. Once people see that a thing is possible, the barrier to entry becomes lower; the impossible becomes feasible.
Base formation completion is one of the most important characteristics one can identify when looking for potential for capital growth. Base formation completion happens for a reason. The Internet of Everything is enormously exciting. Inserting chips, transmitters and cameras into just about everything greatly enhances potential for productivity growth. As the digitisation of the built environment ramps up, the potential for even the most everyday item to be used as a conduit for data transfer is only going to intensify.
This section from Broadcom’s website is worth ruminating on: “Cisco reports that by 2020, the number of connected devices is expected to reach 50 billion –or six devices for every person on earth.”
Over the last month companies that benefit from this connectivity build-out have been completing bases.
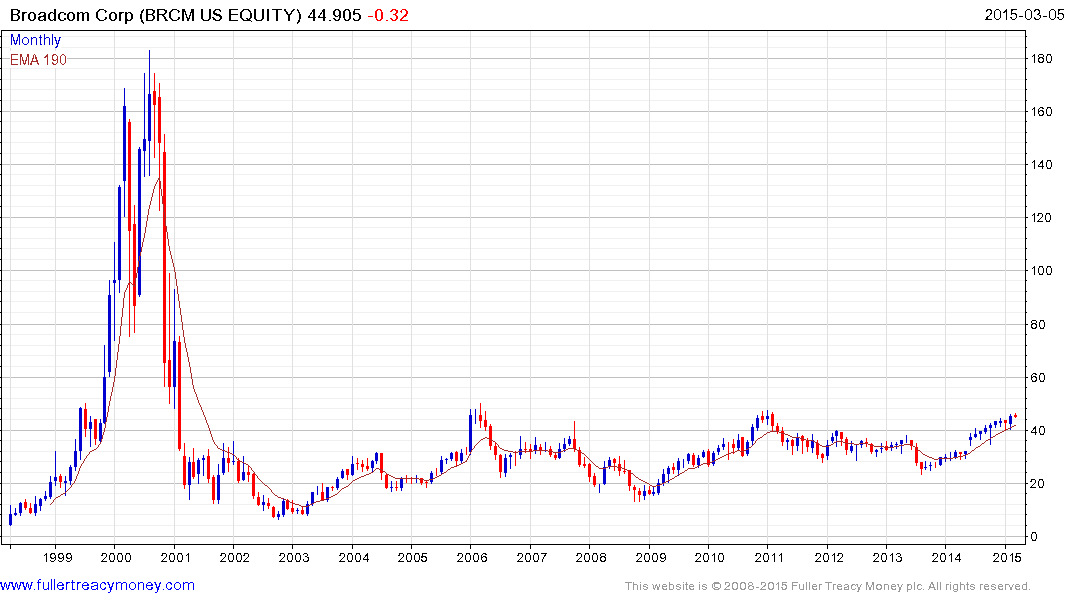
Broadcom is testing the upper side of a 15-year base.
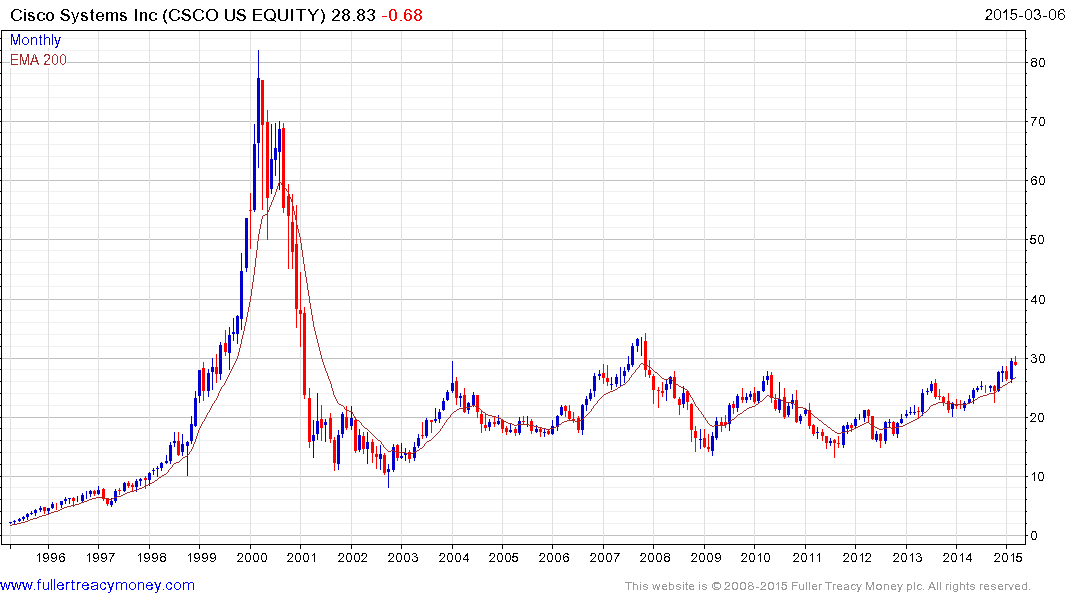
Cisco Systems has a similar pattern.
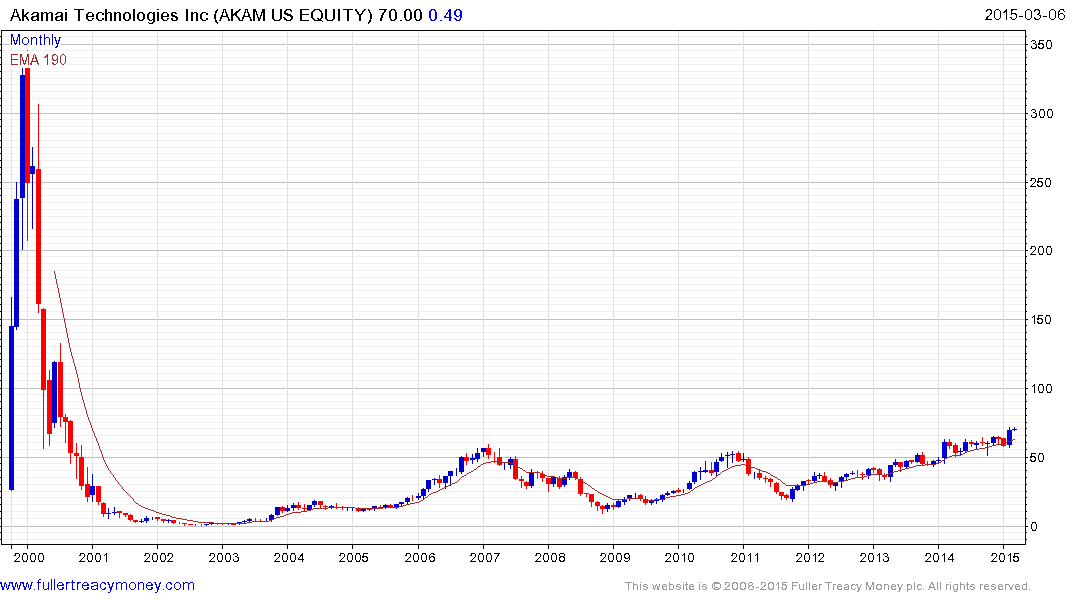
Akamai Technologies completed its lengthy base in February.
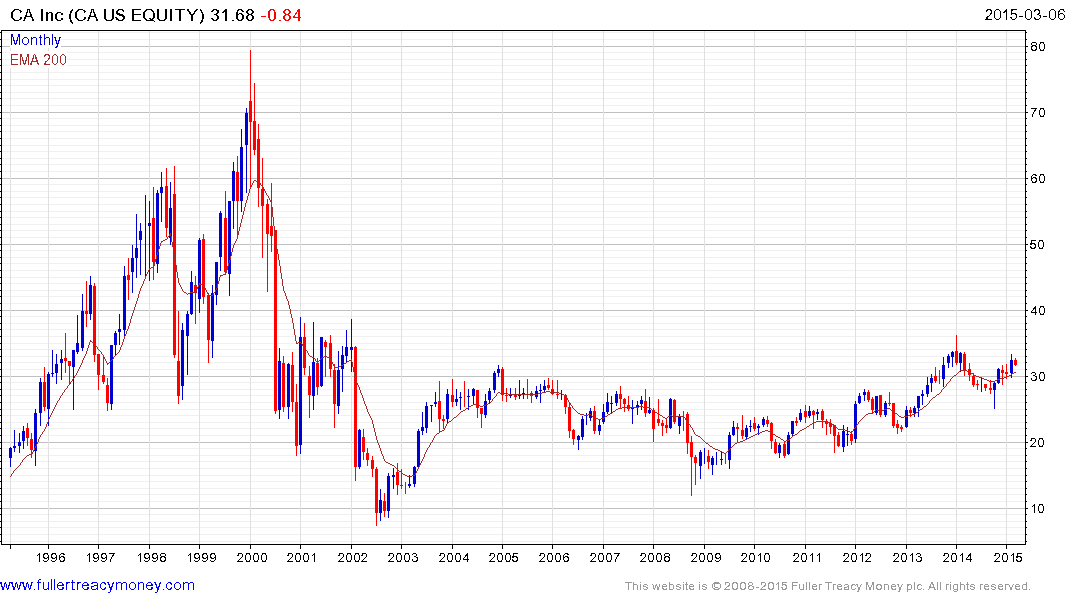
CA Inc. remains in what has been a choppy uptrend since 2008.
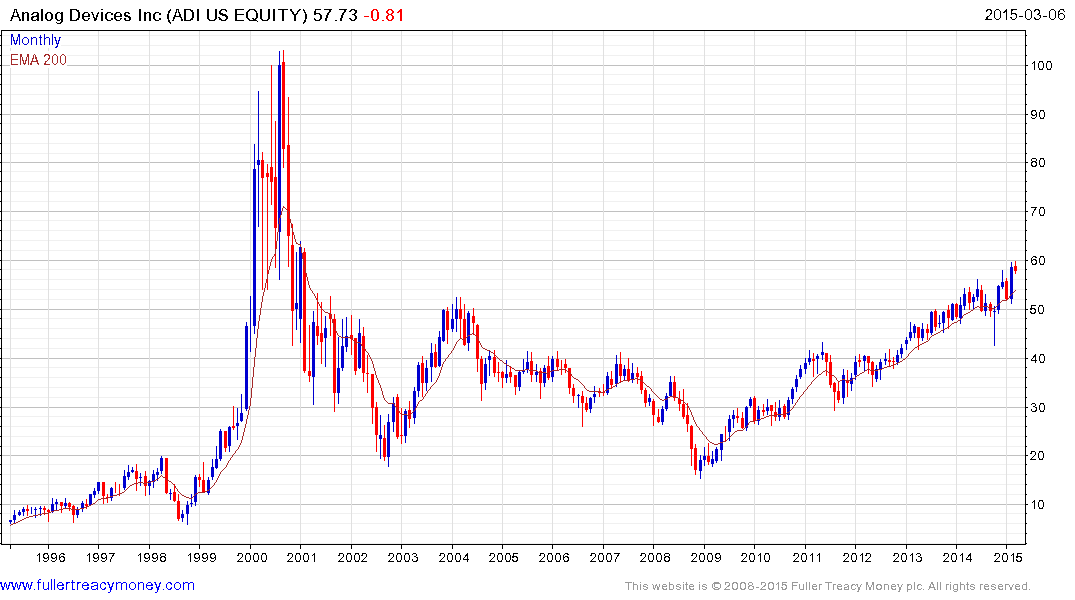
Analog Devices is also in the process of completing a long-term base formation.
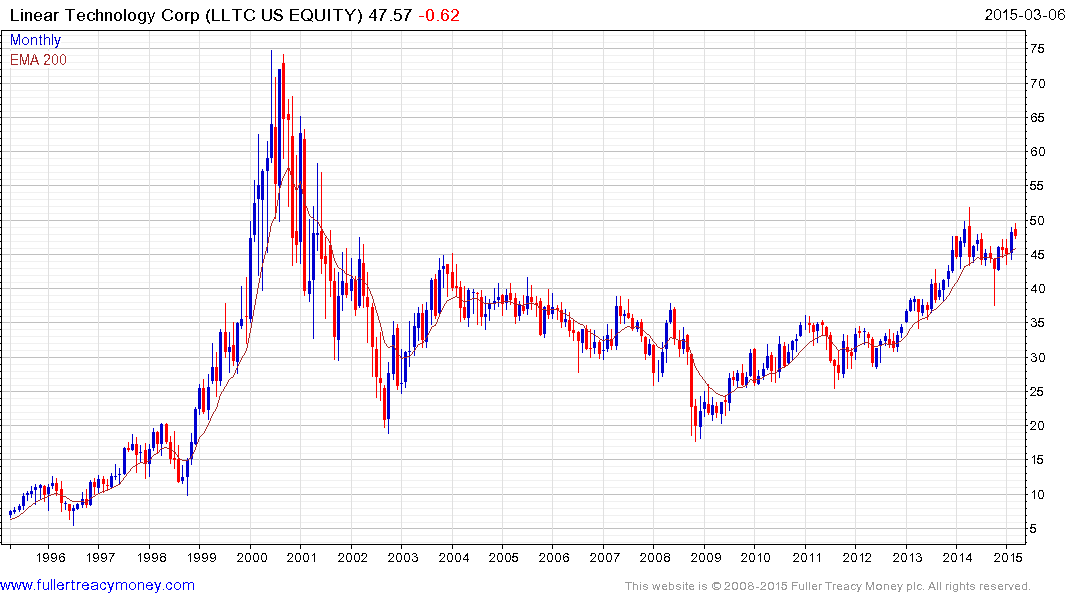
Linear Technologies has a similar pattern.
As companies like Apple, Google and Facebook acquire banking licences and as payments become increasingly tied to one’s cell phone, security remains a growth sector. This article from The Guardian makes a number of additional interesting points.
Clicking through the cyber security sector of the Eoin’s Favourites section of the Chart Library some of the more impressive chart patterns include:
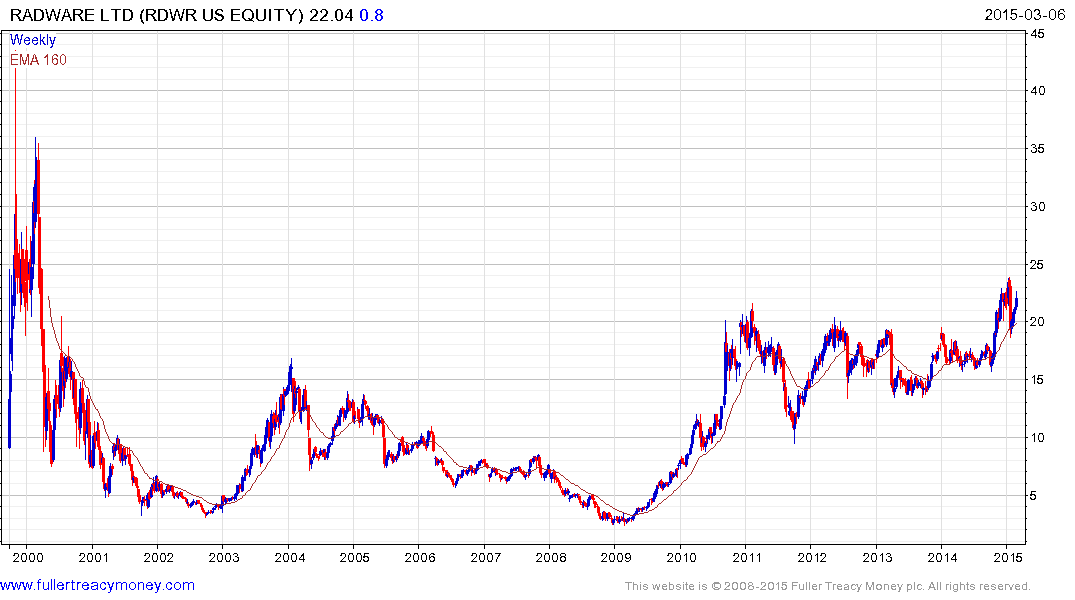
Radware found support in early February at the upper side of a four-year range.
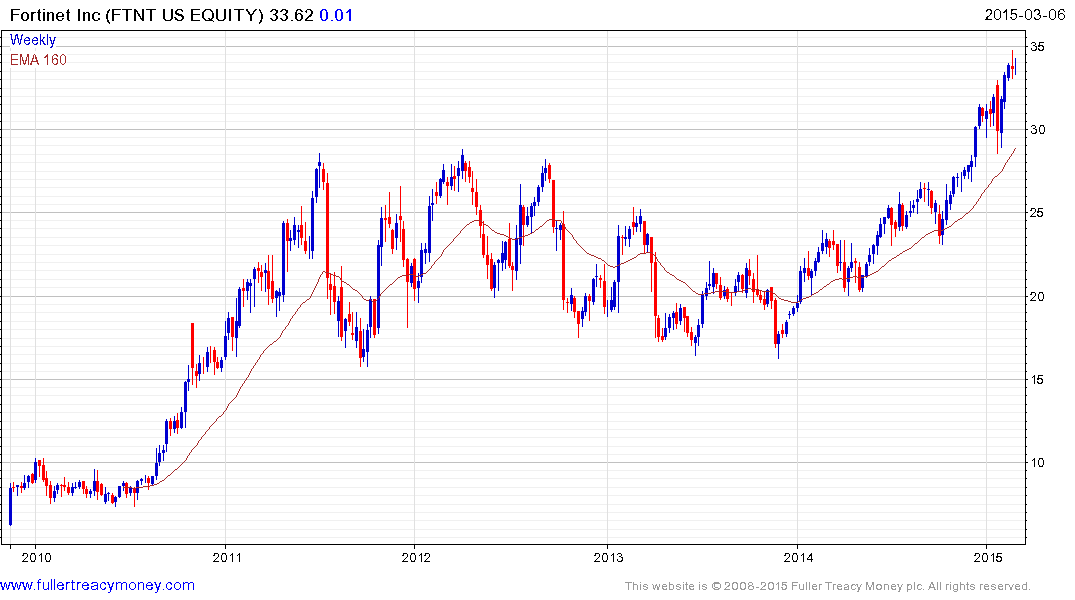
Fortinet broke out to new highs in December and continues to extend its uptrend.
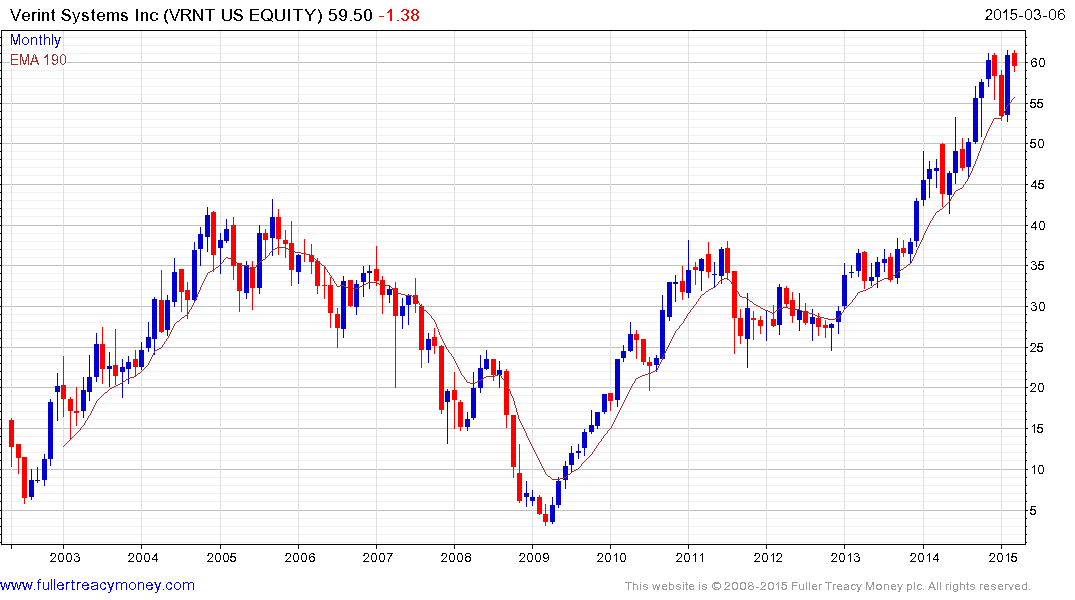
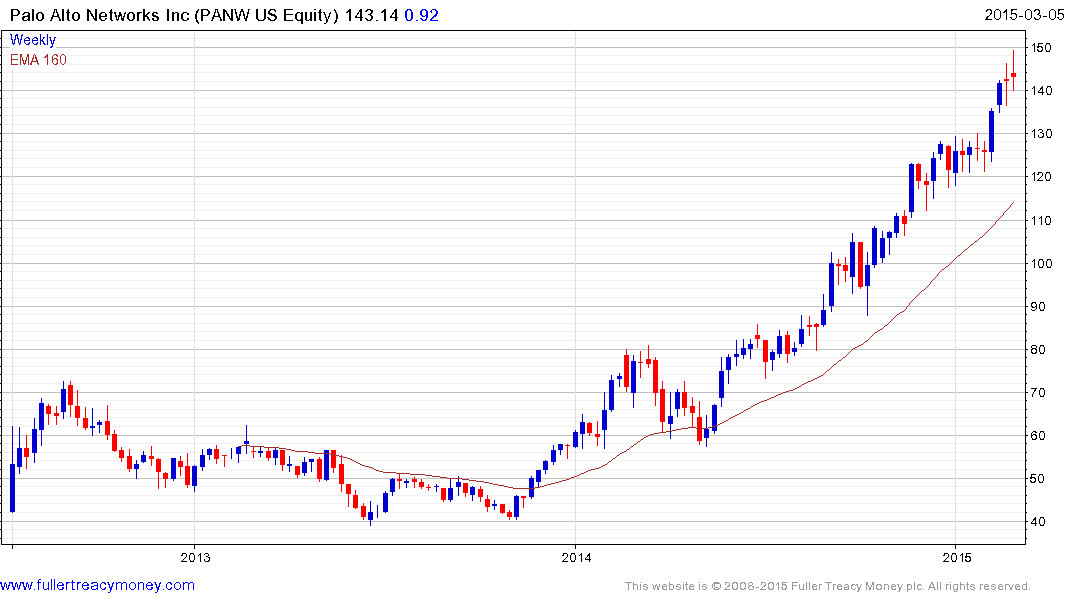
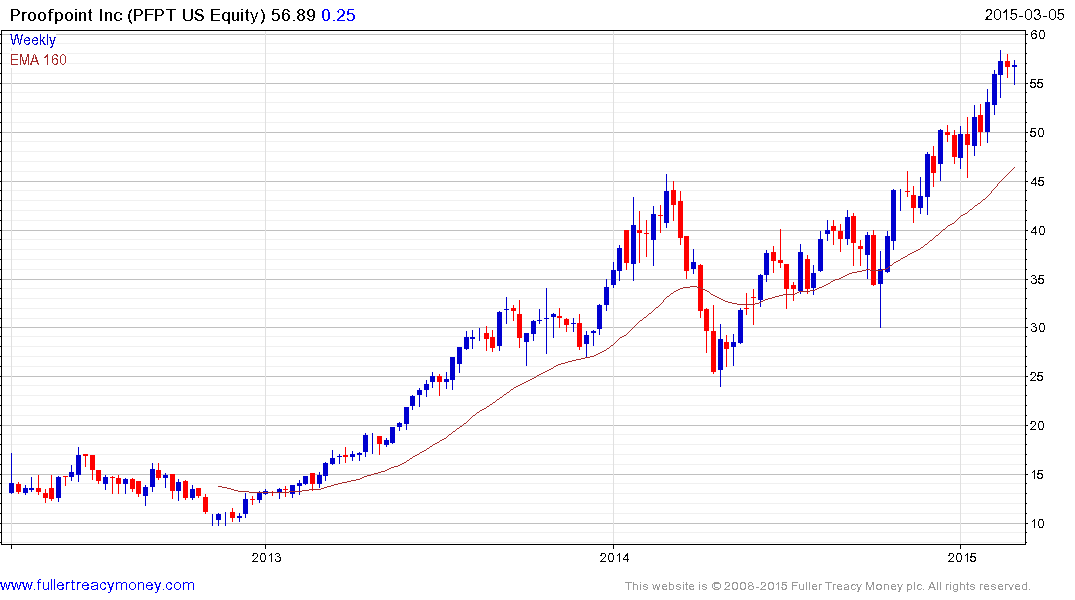
Verint Systems, Palo Alto Networks and Proofpoint remain in consistent uptrends but as susceptible to some consolidation of recent gains.
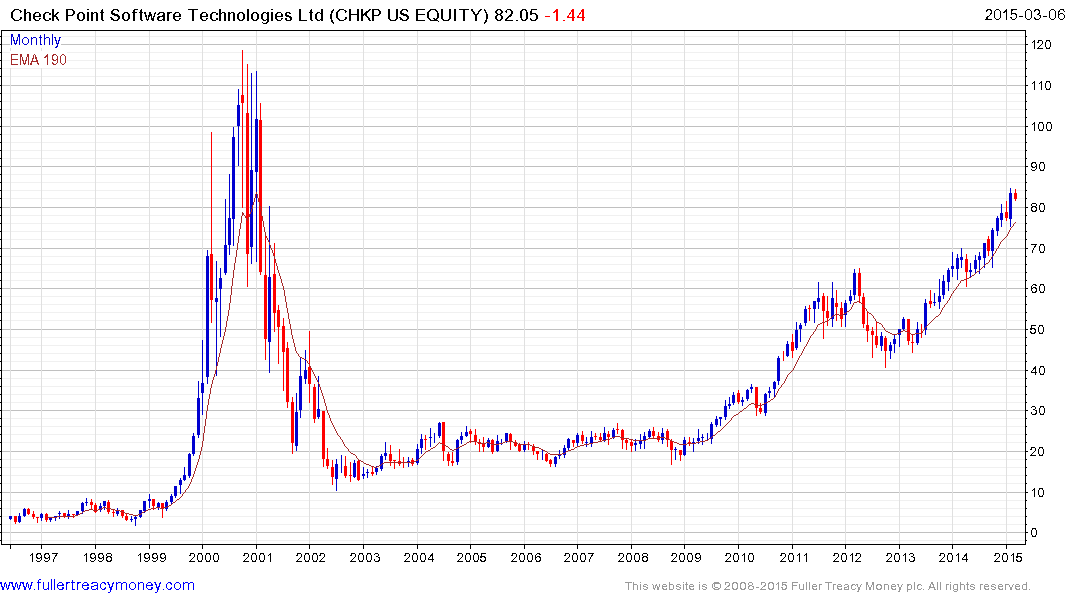
Check Point Software remains a leader but is somewhat overextended at present.
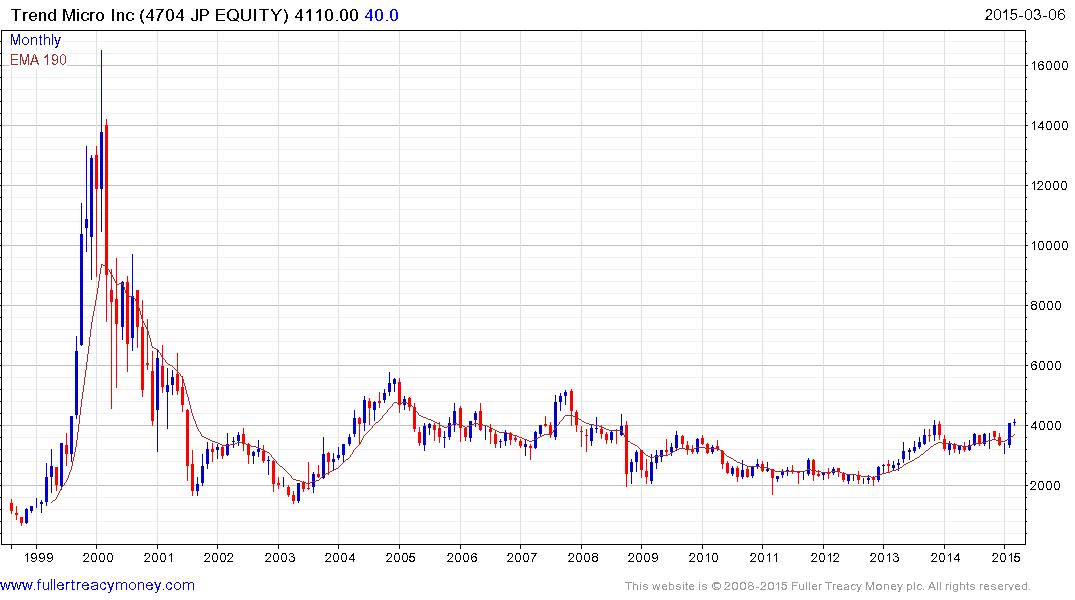
Japan listed Trend Micro is rallying within its long-term base.
Another way to consider the internet security sector is to conclude that breaches are inevitable and
that the only true defence is to insure against loss. As a result companies like Experian offering credit monitoring services have the potential to continue to grow.
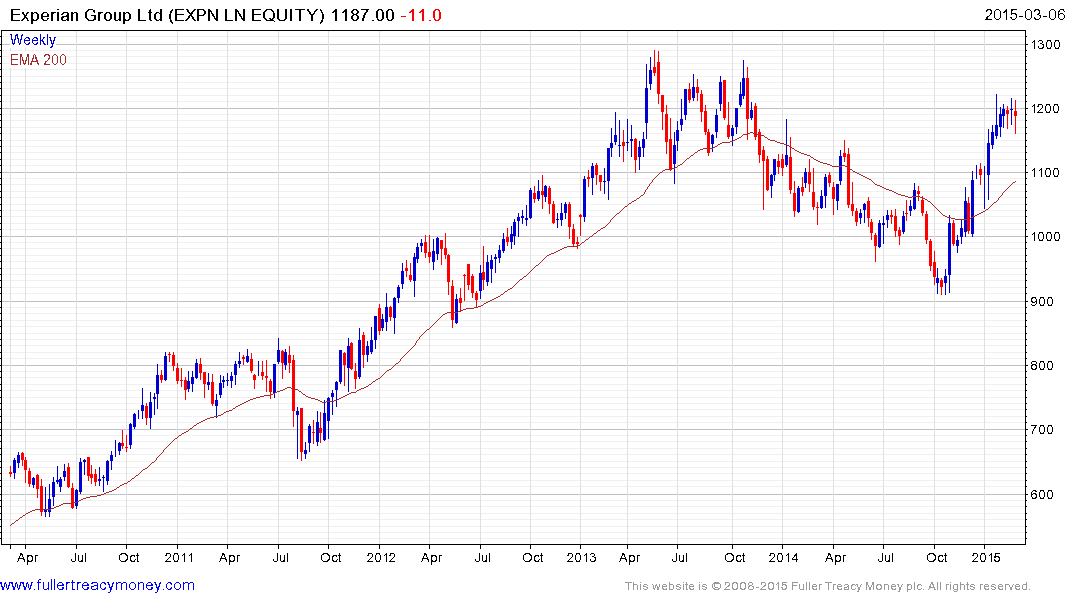
The share rallied in December to break an 18-month progression of lower rally highs and a sustained move below the 200-day MA, currently near 1100p, would be required to question medium-term scope for additional upside.
Back to top


