The Hunt for the Financial Industry's Most-Wanted Hacker
This article by Dune Lawrence may be of interest to subscribers. Here is a section:
ZeuS, meanwhile, has become a permanent gift to the cyber underground. SecureWorks documented attacks that targeted more than 1,400 financial institutions across more than 80 countries—just from 2014 through March 2015. Since the ZeuS source code leak, almost all banking malware has incorporated its features, according to SecureWorks.
“We fight them over there so we don’t have to fight them here” is an outmoded mechanism for containing nefarious criminal elements regardless of whether their motivations are based on religion, greed or both. The fact that Bogachev released his program when he was 22 in 2005, has been free to sell it, post updates and was only identified in 2014 is a testament to the fact that other countries do not share the same concern for private property as we do in the West. This is particularly the case when criminal elements are targeting assets outside their respective countries. This story is based on a private enterprise with money as its goal but of course there are more sophisticated stat-run operations that have additional motivations. The world is quickly moving into a scenario where internet security will become more pervasive not least because the risks have increased.
The vast majority of internet security systems rely either on securing your personal information on your personal device or securing your information at a remote location and giving you some form of secure access. When you try to retrieve your Gmail password, Google now sends you a text message with a code to login. Most European banks have sent third party devices in the mail to their customers which generate unique codes every time the client logs in. This is a major innovation and a necessary additional security step for securing access.
In the cat and mouse game between criminals and security personnel Bitcoin represents a new, potentially powerful, front in security. This brief article from Bloomberg centring on a joint venture between Samsung and IBM suggests the blockchain may be on the cusp of going mainstream. Here is a section:
The blockchain technology is very interesting in general, and it can be applied in a lot of areas,” Rahman said. “Currency, it’s just the first use case. You could imagine that anything, like prescriptions, could be managed with the blockchain technology.”
Samsung Research America usually develops technologies that may be used in commercial products in two to five years, he said, declining to provide further details about the bitcoin project.
Storage Alternative
The bitcoin blockchain could allow for cheaper money transfer and be used for storage of files like songs and videos, which currently require companies to either buy hundreds of servers or lease capacity from other service providers.
Other companies have become interested in the technology. Orange SA’s Silicon Valley-based venture-capital arm has said it’s looking to invest in bitcoin startups. This year Nasdaq OMX Group Inc. licensed its technology to a bitcoin trading company, while the New York Stock Exchange invested in bitcoin startup Coinbase.
Rather than focus on the value of an individual bitcoin, perhaps the more important innovation is in the blockchain ledger which is complex and almost impossible to change a time stamp on. It acts as a record of ownership and transactions. The evolving quantum computing sector has similar potential but is probably farther from widespread release.
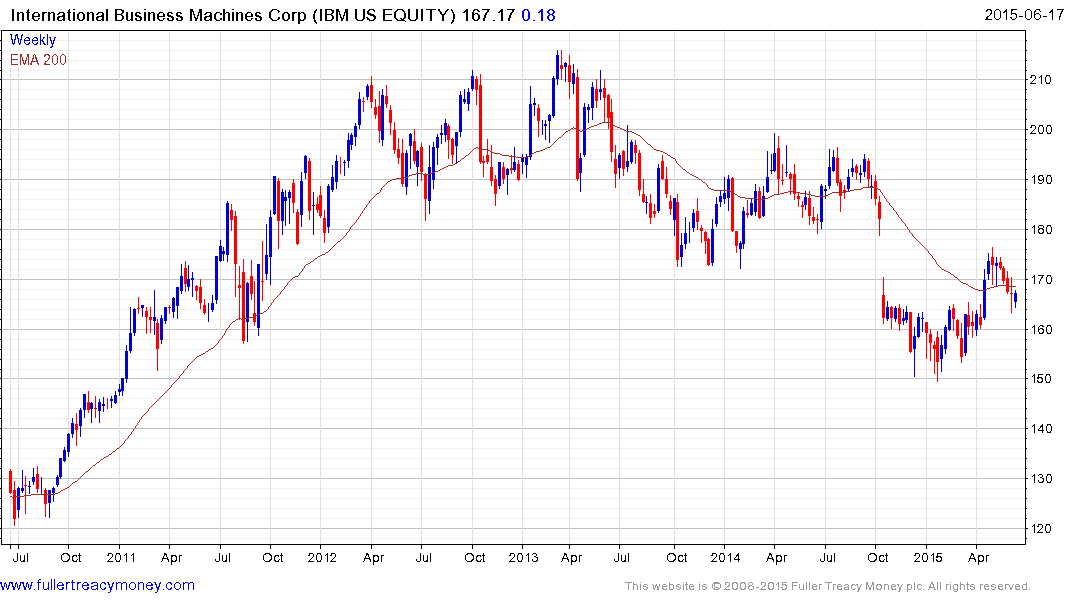
IBM has a long-term record of developing innovative technology but has been less successful at commercialising its creations over the last few years. The share dropped more than 40% from its 2013 peak to the January low. It has held a progression of higher reaction lows since and found at least short-term support this week in the region of $163. A sustained move below that level would be required to question potential for additional higher to lateral ranging.


